MOVEit Transfer App's Third Bug Found During Mass Cl0p Ransomware Attack
Progress Software recently disclosed a number of serious vulnerabilities affecting their MOVEit Transfer tool. The business issued a warning that these flaws might result in data breaches, unauthorised access to the environment, and privilege escalations. The disclosure follows extortion strategies used by the Cl0p cybercrime organisation, which targeted businesses afflicted by the flaws. The specifics of the vulnerabilities, their possible effects on impacted organisations, and the broader ramifications for cybersecurity will all be covered in this article.
Overview of MOVEit Transfer Vulnerabilities:
Three flaws were found in the MOVEit Transfer programme by Progress Software. Two of these flaws were connected to SQL injection attacks, but the third has not yet been given a CVE number. The SQL injection flaws can be used to access the application's database without authorization. A similar risk of privilege escalation and unauthorised access to the environment is also present due to the recently discovered issue.
Progress Software has urged its clients to turn off all HTTP and HTTPs traffic on ports 80 and 443, in order to reduce the dangers brought on by these vulnerabilities. While the firm develops a thorough fix, this interim update tries to safeguard the impacted environments.
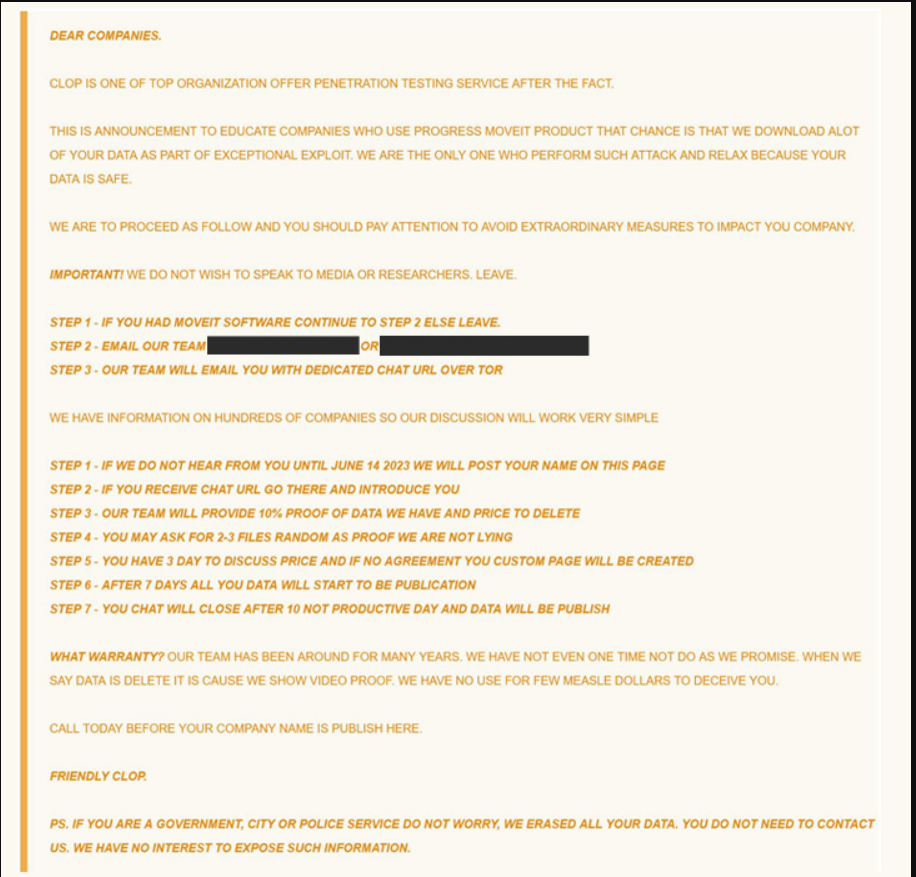
Exploitation by Cl0p Cybercrime Gang and Data Theft:
The Cl0p cybercrime group, which is well-known for its ransomware operations, swiftly took advantage of these flaws and used extortion strategies against the impacted businesses. The group not only attacked private businesses but also various American federal departments, notably the Department of Energy.
The Cl0p actors revealed the scope of the data thefts by listing the names of 27 stolen businesses on a darknet leak page. Multiple well-known organisations are on the list, according to CNN, which emphasises how urgent it is to fix these vulnerabilities right away.
The Clop ransomware gang used one of the vulnerabilities, CVE-2023-34362, as a zero-day vulnerability. Microsoft had been keeping an eye on the exploit since July 2021, it was subsequently discovered. The incident emphasises the value of preventative cybersecurity procedures to find and eliminate new threats.
Impact on Affected Organizations:
The affected organisations would be significantly impacted by the flaws in the MOVEit Transfer application. Proprietary information, client data, and intellectual property of organisations are at danger due to the possibility of unauthorised access to sensitive data and privilege escalation.
The number of possibly compromised organisations is far higher than first thought, claims cybersecurity company ReliaQuest. Approximately 31% of the exposed hosts running MOVEit belonged to financial services firms, followed by the healthcare (16%), IT (9%), and government and military (8%) industries. Nearly 80% of these servers are located in the United States.
Data breaches can have serious and far-reaching repercussions. Affected organisations might experience financial setbacks, harm to their reputations, and legal ramifications. Additionally, customers and stakeholders may stop believing that the company can protect their data, which could have long-term effects on the company.
Platforms that offer cybercrime as a service (CaaS) are widely used, which has considerably increased the number of cyberattacks. The bulk (58%) of malware families spread over MaaS platforms between 2015 and 2022, according to Kaspersky's analysis, are ransomware-related. Botnets, loaders, and backdoors account for 18% of the distribution, while information stealers make for 24% of it.
When MaaS schemes are available, the entry hurdle for attackers with less technical expertise is lowered, allowing them to carry out complex cyberattacks. Since cybercrime has become commodified, even non-expert people can engage in it, posing a greater threat to society as a whole.
One of the main motivating forces behind cybercrime is the desire for financial gain. Cybercriminals engage in illegal actions such as selling stolen data and paying ransoms in order to make money. Because of how connected everything is online, there are countless opportunities for attackers to take advantage of weaknesses.
Numerous organisations are now at danger of data breaches and unauthorised access due to flaws found in Progress Software's MOVEit Transfer programme. The Cl0p cybercrime gang's use of these vulnerabilities underlines the critical need for strong cybersecurity measures and regular software updates. To reduce the danger of cyberattacks, organisations must maintain vigilance, update their systems often, and have thorough security measures in place. To find and prosecute cybercriminals, law enforcement authorities and cybersecurity companies must work together. Organisations may safeguard their sensitive data and defend themselves against developing cyber threats by placing a high priority on cybersecurity and implementing preventative measures.




Comments
Post a Comment