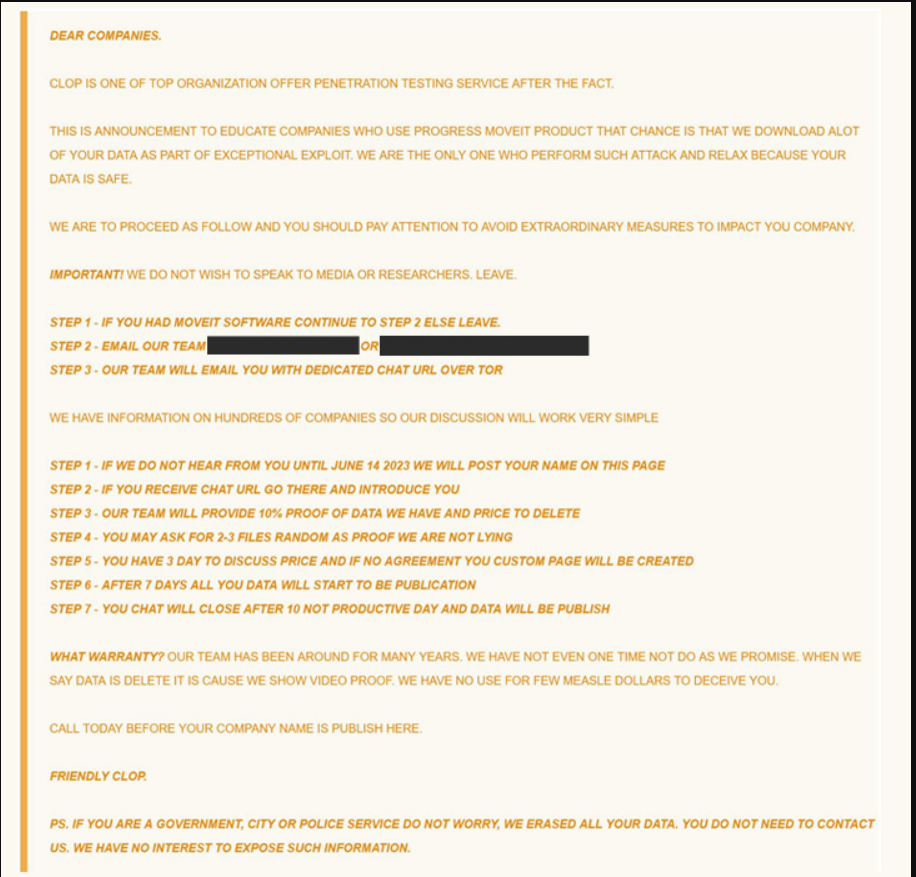
A Framework for Improved Security: Continuous Threat Exposure Management (CTEM)

Acronyms are commonplace in the rapidly developing subject of cybersecurity, and new ones are constantly being created. Continuous Threat Exposure Management, or CTEM, is one of the acronyms that are now popular. Companies implementing CTEM programmes may run into unexpected difficulties that impede their development and cause setbacks. This article seeks to clarify CTEM, its objectives, and the challenges that businesses must overcome to successfully apply it. It's critical to comprehend what Continuous Threat Exposure Management comprises before diving into the difficulties. CTEM is not a technology or a specific product that suppliers sell. Instead, it's a constant 5-stage programme or framework made to assist organisations in tracking, assessing, and lowering their level of exploitability. Its goal is to deliver a standardised and practical security posture correction and improvement plan that corporate executives can...